Having a strong security stack is no longer optional—it is a mandate. Companies are under constant pressure to ensure data confidentiality, access governance, and auditability across all applications. With compliance frameworks such as SOC2, HIPAA, and ISO 27001 demanding stronger controls and transparency, organizations require systems that provide not only tight access management but also full visibility into security configurations.
Recognizing this need, our team has introduced two powerful new features into its platform’s enterprise security toolkit: System Security Summary and User Security Summary. These tools make it easy for administrators and security officers to understand, manage, and audit access control across the FlowWright environment in real time. Let's break it down...
Why Security Transparency Matters in Software
Workflow platforms manage a range of business-critical artifacts: process definitions, instances, forms, reports, tasks, APIs, and more. In complex systems with hundreds of users and thousands of objects, the web of access control can quickly become opaque and hard to track.
Without visibility:
- Admins struggle to answer basic questions like "Who has access to this form?" or "What can this user do in the system?"
- Security reviews become time-consuming and error-prone.
- Insider threats go undetected.
- Compliance audits are a nightmare.
Our new security summaries solve these issues by providing real-time, structured insights into access distribution at both macro and micro levels.
"Out of 1,200 form instances, 97 are publicly accessible with no group/user-level restrictions—this may violate internal data access policy."
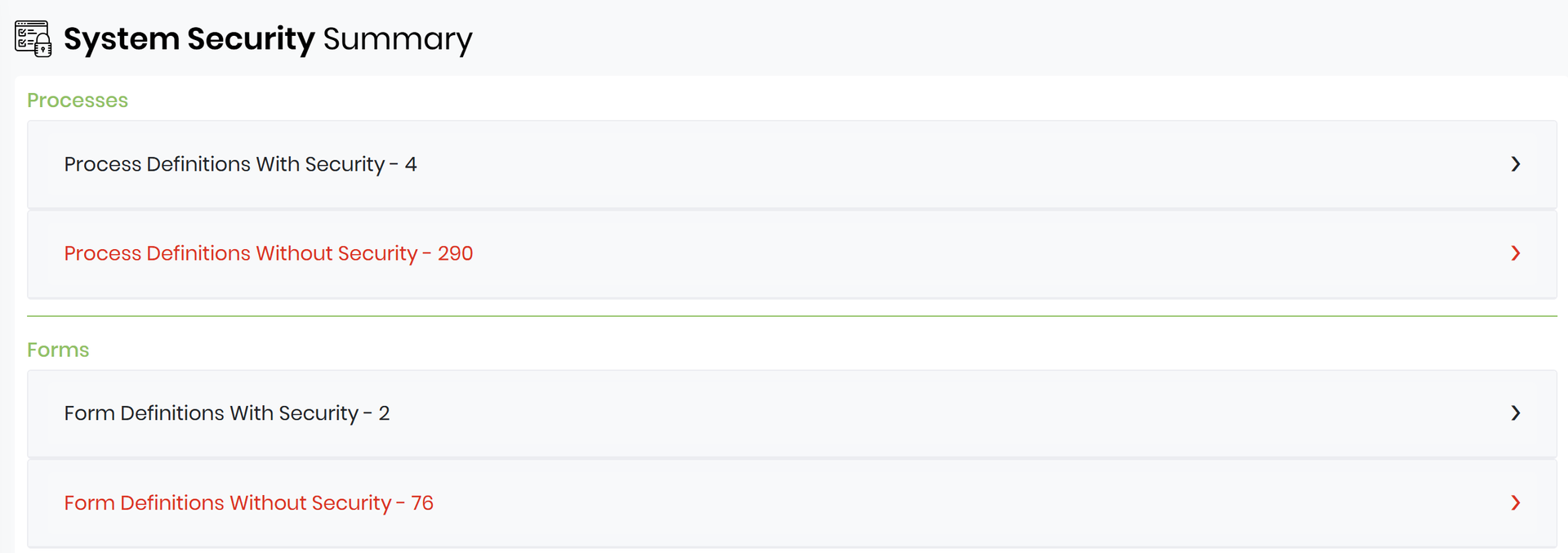
System Security Summary: The Big Picture View
The System Security Summary is designed for global visibility. It gives administrators a holistic view of who has access to what across the entire instance. This includes:
- Process Definitions
- Process Instances
- Form Definitions
- Form Instances
- Dashboards
- Reports
- Tasks
- Application modules
- Folders
What It Shows
This summary is a dashboard-style report that aggregates and visualizes access control statistics:
- Total number of secured items in each category (e.g., 820 Process Definitions, 450 Forms).
- Number of users and groups with access to each item type.
- Breakdown of access levels (View, Modify, Execute, Admin).
- Orphaned items with no assigned access.
- Public vs. restricted items, useful for identifying overly permissive objects.
Use Cases
- Security Audits: Instantly generate reports for auditors showing item-level access across the system.
- Access Risk Analysis: Spot potential overexposure (e.g., 50 users with Admin access to a critical process).
- Compliance Review: Demonstrate that segregation of duties and least-privilege access are enforced.
- Cleanup & Optimization: Identify unused or misconfigured permissions.
Example Insight
This level of intelligence enables proactive governance and eliminates blind spots.
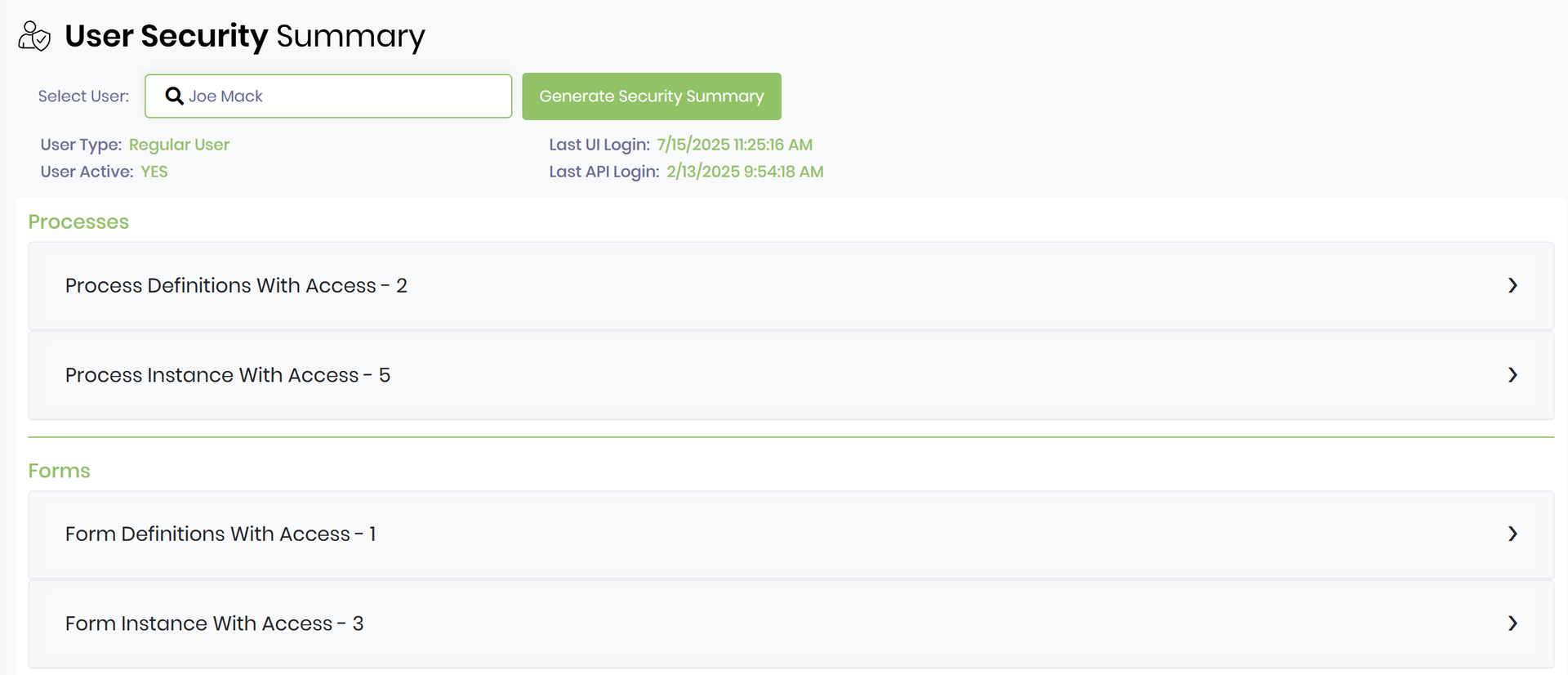
User Security Summary: Drill Into Individual Users
While the system view helps understand access in aggregate, the User Security Summary flips the lens to focus on individual users.
With a few clicks, an admin can select any user and see a detailed list of:
- All items the user has access to, grouped by type.
- How access was granted (direct, group membership, folder inheritance).
- Level of access for each item (View/Modify/Execute/Admin).
- Groups the user belongs to.
- Role-based vs. explicit permissions.
This functionality is essential for user-level audits, access reviews, and incident response.
Use Cases
- Onboarding/Offboarding Review: Ensure new users are provisioned correctly and former employees have had all access removed.
- Least Privilege Validation: Confirm that users only have what they need.
- Investigate Suspicious Activity: Trace what a specific user had access to in case of a breach or policy violation.
- Role Comparison: Compare access across users with similar roles for consistency.
Example Insight
"User ‘jsmith’ has Modify access to 23 process definitions and Execute access to 12 reports via group ‘Supervisors’, plus one direct Admin access to a restricted folder."
Designed for Enterprise-Grade Security
These new summaries are not just reports—they’re part of FlowWright’s enterprise-grade security framework, designed for:
- Scalability: Works even in systems with thousands of items and users.
- Performance: Summaries are built with optimized queries and data structures for fast rendering.
- Interactivity: Export to CSV, filter by access type, drill down by user or item.
- Audit Readiness: Generate access reports that align with regulatory standards.
- Zero Trust Alignment: Visualize trust boundaries and least privilege compliance.
Built-In Features and Integrations
The summaries integrate natively with FlowWright's broader security model:
- LDAP/AD integration: Access mapping works with external identity providers.
- Folder Security Inheritance: Clearly identifies inherited permissions vs. explicit ones.
- Access Logs: Tie in with FlowWright’s audit logging to correlate access with activity.
- Role-based Access Control (RBAC): Highlights role-derived access for users.
How Customers Benefit
1. Easier Security Reviews
IT security teams and compliance officers can export both summaries during audits and easily demonstrate access control adherence without manually assembling reports from logs or databases.
2. Faster Incident Response
If a security breach is suspected, administrators can instantly review what a user or group had access to, reducing investigation time from hours to minutes.
3. Better Governance
Access risks such as dormant users with excessive privileges or improperly secured workflows become easy to detect and correct.
4. Reduced Manual Effort
Security reviews that previously took hours of SQL queries and cross-referencing now take minutes with a few clicks.
Forward-Looking Security
With FlowWright’s push into AI-powered process automation and low-code application building, the surface area for access expands. These summaries are foundational for enabling:
- AI-driven security alerts based on access pattern anomalies.
- Dynamic access scoring for risk-based authentication.
- Automated access reviews and certification campaigns.
This is not just about visibility—it’s about creating an intelligent security posture that evolves with your business.
Security without visibility is just wishful thinking. FlowWright’s new System Security Summary and User Security Summary bring clarity to complexity by giving enterprise administrators a centralized, actionable view of who can access what.
Whether you’re managing a small team or securing workflows across global departments, these tools empower you to:
- Reduce security risk
- Increase compliance
- Accelerate access reviews
- Simplify governance
This new functionality is our commitment to enterprise-grade security—and another reason why we remain the trusted workflow platform for secure, scalable, and intelligent business process automation by teams all around the globe.
FlowWright Workflow Automation is Secure by Design. Now You Can Prove It.
Need help using the summaries or configuring secure access in your environment? Contact us for a demo or security consultation.







